Physical tokens, such as the Fast Identity Online 2 (FIDO2)-based token or security key, are another passwordless option that can be used. While the Microsoft Authenticator app is a soft token, FIDO2 tokens are physical pieces of hardware that are typically either connected to the computer (in the form of a USB device) or that communicate wirelessly (via Bluetooth or NFC).
You can access the security key logon process during a browser session by selecting the Sign in with
Windows Hello or a security key option from the sign-in page, as shown in Figure 5.5:
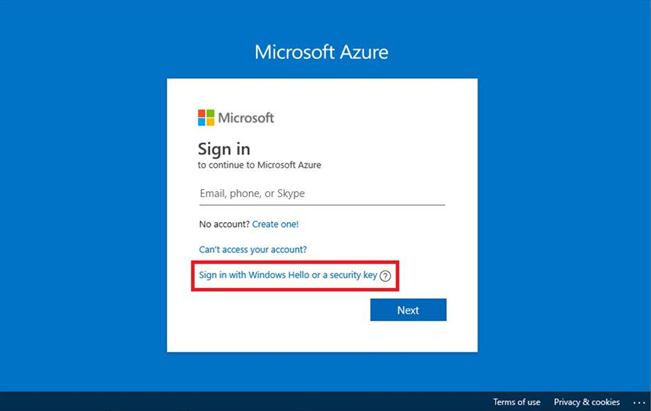
Figure 5.5 – Passwordless authentication dialog with a FIDO2 security token
The data flow for a FIDO2-based logon follows a similar pattern as both WHFB and the Microsoft Authenticator app. For example, to log in to a device using FIDO2, this process outlined in Figure 5.6 is followed:
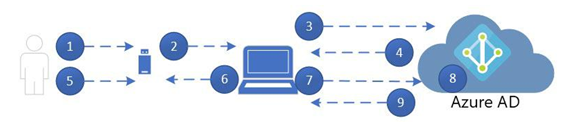
Figure 5.6 – FIDO2 authentication sequence
- The user plugs in a FIDO2 security key.
- Windows detects the security key.
- Windows sends an authentication request to Azure AD.
- Azure AD responds by sending a nonce back to the logon device.
- The user authenticates to the FIDO2 key, unlocking the secure storage area containing the private key.
- The FIDO2 key signs the nonce with the private key and sends it to Windows.
- Windows generates a PRT request and sends it with the signed nonce to Azure AD.
- Azure AD verifies the signed nonce with the FIDO2 device’s public key.
- Azure AD returns the PRT to the logon device.
FIDO2, like Windows Hello, has specific requirements for supported hardware.
Supported FIDO2 Security Tokens
You can see an up-to-date list of supported FIDO2 security keys or tokens here: https:// learn.microsoft.com/en-us/azure/active-directory/authentication/ concept-authentication-passwordless#fido2-security-key-providers.
As you’ve seen from the diagrams, each of the passwordless options (Windows Hello, Microsoft Authenticator App, and FIDO2) follows a similar authentication workflow, based on public key infrastructure.
Comparison
Now that you have explored the different passwordless options available for Microsoft 365, let’s look at some information that will help you choose the appropriate solution. Table 5.1 describes some basic features and requirements for each authentication scheme.
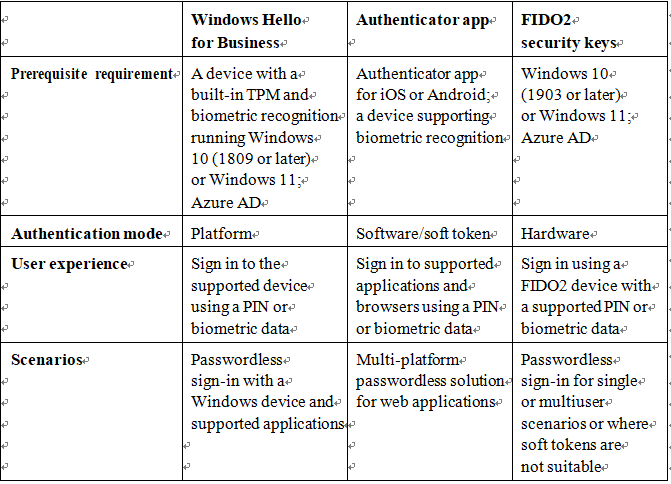
Table 5.1 – Authentication method comparison table
It’s also important to consider the various end user scenarios that your organization utilizes to ensure you’re recommending an appropriate mechanism based on your real-world use cases. Table 5.2 describes a few example scenarios:
Table 5.2 – Passwordless logon scenarios
With that information in hand, it’s time to look at the implementation aspects.