If you have configured Azure AD Connect or Azure AD Connect Cloud sync with your organization, you can manage SSPR integration features, as shown in Figure 5.23:
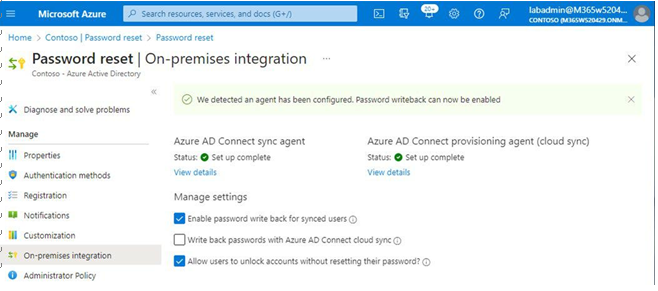
Figure 5.23 – On-premises integration
It’s important to note that the Enable password write back for synced users option only modifies the behavior of Azure AD sending password reset data back to the on-premises environment, effectively stopping on-premises integration. It does not modify the on-premises Azure AD Connect configuration.
Next, you’ll look at the features of Azure AD password protection.
Implementing and Managing Azure AD Password Protection
Azure AD password protection is a set of features designed to limit the effects of common password attacks. To view the password protection configuration, navigate to Azure Active Directory | Security | Authentication methods and select Password protection. See Figure 5.24:
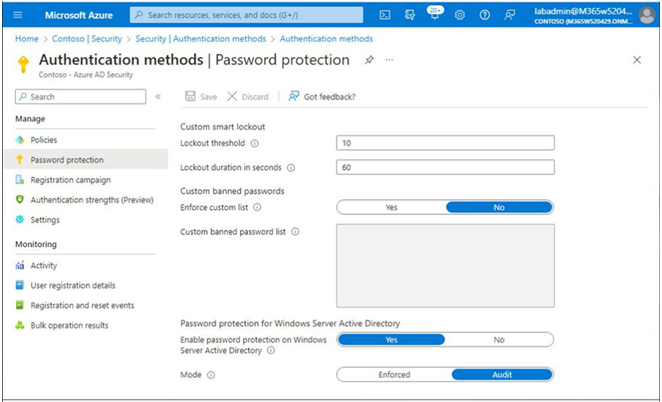
Figure 5.24 – Password protection
There are three groups of settings to configure:
• Custom smart lockout
• Custom banned passwords
• Password protection for Windows Server Active Directory
Let’s briefly examine each set of configurations.
Custom smart lockout
The smart lockout settings determine how Azure Active Directory handles failed login attempts. Lockout threshold is the number of times in a row a user can enter a bad password before getting locked out. By default, Lockout threshold is set to 10 in Azure Worldwide (sometimes referred to as Commercial or Public) and Azure China 21Vianet tenants, while it is set at 3 for Azure US for Government customers. Figure 5.25 depicts the error message displayed when the bad password threshold is met:
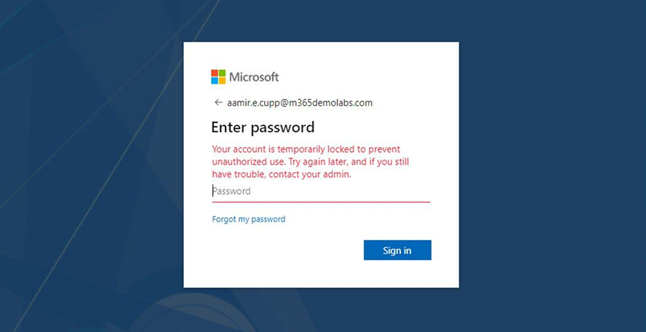
Figure 5.25 – Account lockout
Lockout duration in seconds only specifies the initial lockout duration after the lockout threshold has been reached. Each subsequent lockout increases the lockout duration. As a security mechanism, Microsoft does not publish the rate at which the duration increases.
Custom banned passwords
While Microsoft recommends moving toward passwordless authentication as a primary mechanism, passwords are still required to be configured in a number of scenarios. To help minimize using well-known, weak, or easily guessable passwords, you can choose to specify a custom list of words that you want to exclude from being used as passwords. For example, you may wish to include your organization’s name or abbreviation, products or services offered by your organization, or local sports teams.
To enable the option, slide the Enforce custom list toggle to Yes, and then add up to 1,000 banned words in the Custom banned password list text area. The list is not case-sensitive. Azure AD automatically performs common substitutions (such as 0 and o or 3 and e), so you do not need to think of all of the possible ways a word can be represented.