For most organizations, security defaults are a good choice for configuring broad baseline security policies. Security defaults make the following security changes:
• Requiring all users to register for multifactor authentication
• Requiring administrators to perform multifactor authentication upon sign-in
• Requiring users to do multifactor authentication when necessary
• Blocking basic authentication and other legacy authentication protocols
• Requiring administrators to perform multifactor authentication when accessing privileged resources, such as the Azure portal, Azure PowerShell, or the Azure CLI
Security defaults can be modified by users with the Global Administrator, Conditional Access administrator, or Security administrator roles. Security defaults can be enabled or disabled using the following process:
- Navigate to the Azure portal (https://portal.azure.com).
- Select Azure Active Directory.
- Under Manage, click Properties.
- Scroll to the bottom of the page and click Manage security defaults.
- On the Security defaults flyout, select either Enabled or Disabled and click Save.
If you are going to configure Conditional Access policies, you should disable security defaults. If you are not going to configure Conditional Access policies, you should enable security defaults.
Further Reading
For more information on the impact of security defaults, see https://learn. microsoft.com/en-us/azure/active-directory/fundamentals/ concept-fundamentals-security-defaults.
Conditional Access
Conditional Access provides the most fine-grained control when managing the multifactor authentication requirements for your organization. Conditional Access policies can be configured from the Azure portal.
To access the Conditional Access configuration page, follow these steps:
- Navigate to the Azure portal (https://portal.azure.com).
- Select Azure Active Directory | Security | Conditional Access, and then choose Policies.
You can create new policies or use one of the Microsoft-provided 14 sample Conditional Access policy templates. Policies created with a template can be modified once they have been deployed to your tenant.
To configure a template-based policy, follow these steps:
- From the Conditional Access | Policies page, as shown in Figure 5.28, select New policy from template (Preview):
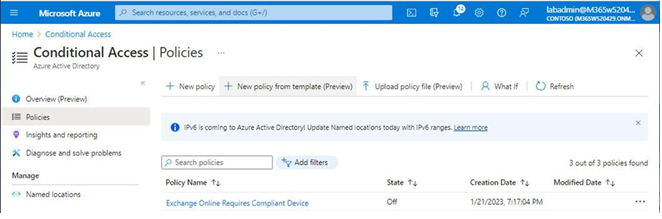
Figure 5.28 – Creating a new Conditional Access policy from a template
- Select one of the templates, such as Require multifactor authentication for all users, and click Review + create, as shown in Figure 5.29:
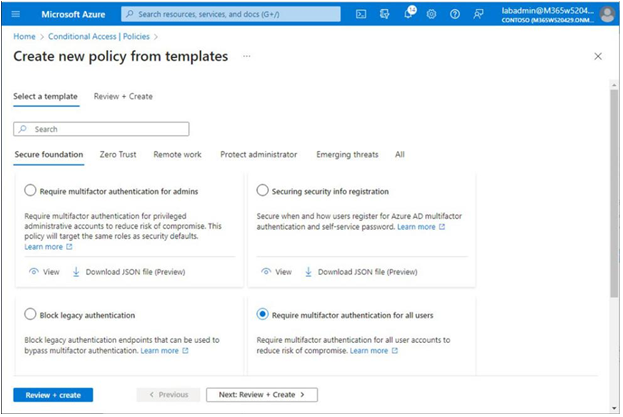
Figure 5.29 – Selecting a template
- Review the settings and click Create.
Policies created through the templates cannot be modified during creation, with the exception of Enforcement mode. All template-based policies are configured in Report only mode, which can be toggled during creation. The user creating the policy is excluded from the policy to prevent accidental lockout.
After the template policies have been configured, you can edit the scope and conditions for the policy like manually created policies.
Further Reading
For more information on Conditional Access templates, see https://learn.microsoft. com/en-us/azure/active-directory/conditional-access/concept-conditional-access-policy-common.
With the exception of Windows Hello, passwordless sign-in methods (such as the Microsoft Authenticator app or FIDO2 security keys) will require users to register for multifactor authentication.