This settings area allows you to extend the custom banned password list to your on-premises infrastructure. There are two components:
• Azure AD Password Protection DC agent, which must be installed on domain controllers.
• Azure AD Password Protection proxy, which must be installed on at least one domain-joined server in the forest. As a security best practice, Microsoft recommends deploying it on a member server since it requires internet connectivity.
In this configuration, the Azure AD Password Protection proxy servers periodically retrieve the custom banned password list from Azure AD. The DC agents cache the password policy locally and validate password change requests accordingly.
If Enable password protection on Windows Server Active Directory is configured as Yes, then you can choose what mode to process password change requests. They can be processed in Audit mode (where changes or logged) or Enforced mode, where password resets are actively evaluated against the banned password list and rejected if they do not meet the requirements.
Further Reading
To view detailed steps for deploying password protection on-premises, see https://learn. microsoft.com/en-us/azure/active-directory/authentication/ concept-password-ban-bad-on-premises.
Configuring and Managing Multifactor Authentication
Configuring users for multifactor authentication can increase the security posture of your Microsoft 365 environment, in addition to protecting any apps that use Azure AD for identity and authentication. In this section, you’ll look at configuring multifactor authentication for your tenant.
Per-User Multifactor Authentication
If multifactor authentication was configured in your tenant prior to October 2019, it may have been configured using the legacy multifactor authentication scheme. Prior to newer technologies, Legacy
Azure MFA was enabled on a per-user basis by manually updating each user’s account to enforce the use of MFA.
Prior to implementing either Microsoft-managed security defaults or Conditional Access policies, you will need to disable the legacy per-user MFA. Having per-user MFA enabled while configuring a Conditional Access policy that prompts for MFA may cause unintended or unexpected MFA prompts.
Note
You should only configure one mechanism for multifactor authentication to avoid unexpected behaviors, such as users being prompted for MFA in scenarios where they previously satisfied multifactor authentication requirements or were accessing resources from trusted locations. Microsoft recommends discontinuing the use of per-user MFA and using Conditional Access policies instead.
To disable per-user multifactor authentication, follow these steps:
- Navigate to the Microsoft 365 admin center (https://admin.microsoft.com).
- Expand Users and select Active users.
- Select Multi-factor authentication:
Figure 5.26 – Active users page
- If your tenant already has Conditional Access policies, you may need to select the Legacy per-user MFA link to launch the legacy multi-factor authentication page.
- On the multi-factor authentication page, as shown in Figure 5.27, configure the per-user MFA status to Disabled for users that have Enforced or Enabled set. You can select multiple users, but can only multi-select users that have the same MFA status type:
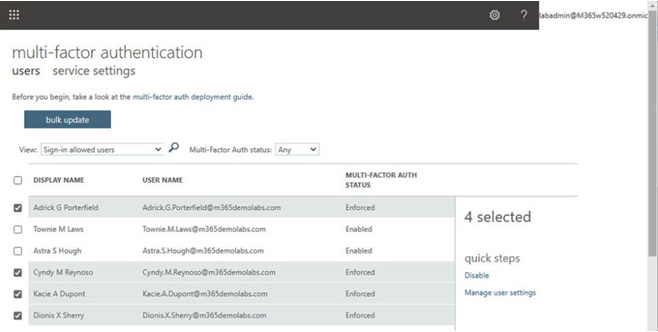
Figure 5.27 – Selecting users
Once per-user MFA is disabled, you can configure security defaults or Conditional Access policies.
Leave a Reply