Microsoft’s recommended solution for passwordless authentication is Windows Hello for Business (WHFB). It’s designed for users that have their own dedicated PC. When logging on, the user presents a biometric or PIN code to unlock the device.
WHFB supports a variety of biometric logons, including facial recognition and fingerprint scanners. Devices configured to use Windows Hello (such as the one shown in Figure 5.1) can be recognized because they have the Windows Hello smiley face greeting at the top:
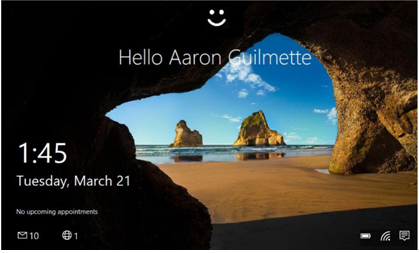
Figure 5.1 – Windows Hello for Business sign-on screen
After configuring Windows Hello, the sign-in flow follows this sequence, as depicted in Figure 5.2:
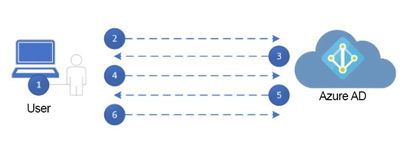
Figure 5.2 – Windows Hello authentication sequence
1. The user signs in with either a biometric or PIN (if the configured biometric input can’t be accessed), which unlocks the WHFB private key. The key is then passed to the Cloud Authentication security support provider, also known as the Cloud AP, part of the on-device security package.
2. The Cloud AP requests a nonce (single-use random number) from Azure AD.
3. Azure AD sends the nonce to the Cloud AP on the endpoint.
4. The Cloud AP signs the nonce with the user’s private key and returns the signed nonce to Azure AD.
5. Azure AD decrypts and validates the signed nonce with the user’s public key. After it’s validated, Azure AD issues a primary refresh token (PRT) with the session key, encrypts it using the device’s public transport key, and sends that to the Cloud AP.
6. The Cloud AP decrypts the PRT/session key using the device’s transport private key and then uses the Trusted Platform Module (TPM) to store the session key.
7. The Cloud AP returns a success response to Windows, allowing the user to log in to complete.
WHFB is available to be deployed as a cloud-only or hybrid identity solution and can be used for both Windows logon as well as logon to Microsoft 365 services. Windows Hello-based authentication is tied to a unique device, meaning you have to set it up individually for each device that you will be using.
Microsoft Authenticator App
Many administrators and users are already familiar with the Microsoft Authenticator mobile device app, after using it for multifactor authentication. The Authenticator app can also be used as a passwordless sign-in option. When used as a passwordless option, Microsoft Authenticator can use number-matching, where the sign-in screen displays a number that the user enters and confirms with their PIN or biometric data. See Figure 5.3:

Figure 5.3 – Passwordless authentication dialog with Microsoft Authenticator
The data flow using the Authenticator app follows the same general pattern as Windows Hello, as shown in Figure 5.4:
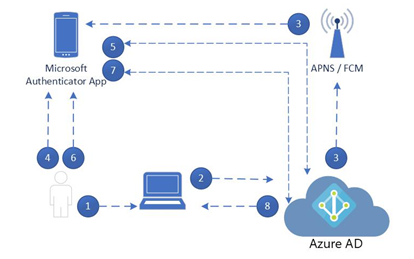
Figure 5.4 – Microsoft Authenticator authentication sequence
1.The user enters their username on the device.
2. Azure AD detects that the user is configured for passwordless authentication.
3. Azure AD sends a notification to the Authenticator app on the user’s configured Apple or Android device.
4. The user launches the Authenticator app.
5. The Authenticator app connects to Azure AD and receives the proof-of-presence challenge and the nonce.
6. The user completes the challenge on their mobile device and then confirms their identity with biometric data or a PIN, unlocking the private key.
7. The private key is used to sign the nonce and the Authenticator app returns the data to Azure AD.
8. Azure AD decrypts the data with the user’s public key, performs validation, and then returns the sign-in token to the original device where the logon was started.
Whereas WHFB has specific hardware requirements (such as a Windows Hello-compatible camera or fingerprint reader), passwordless using Microsoft Authenticator has a very low barrier to entry. The Authenticator app is free for iOS and Android devices and works not only with Microsoft 365 services but also any service that supports a soft-token app or device.
Further Reading
In addition to the traditional Microsoft Authenticator application, Microsoft has also released Authenticator Lite as part of Outlook. For more information, see https://learn. microsoft.com/en-us/azure/active-directory/authentication/how-to-mfa-authenticator-lite.
Leave a Reply